OAuth 2.0 :- Authorization Server
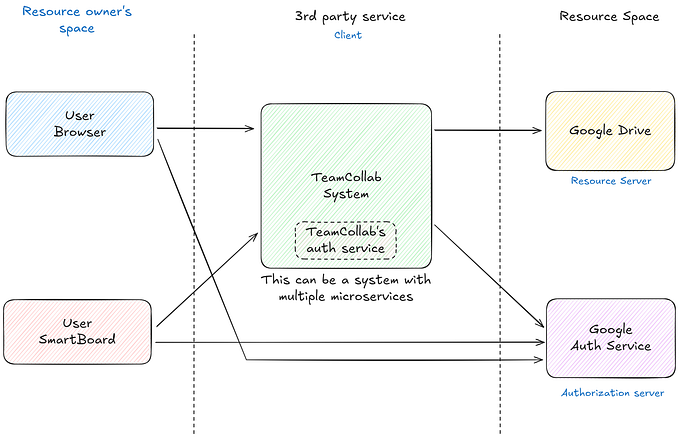
Lets start with a recent example. Assume you need to post an image to Facebook that is stored in Google Drive. You must first log into Google Drive and download the image locally before uploading it to Facebook. What if we could redirect Facebook to Google Drive and upload images there? In that instance, OAuth 2 is engaged.
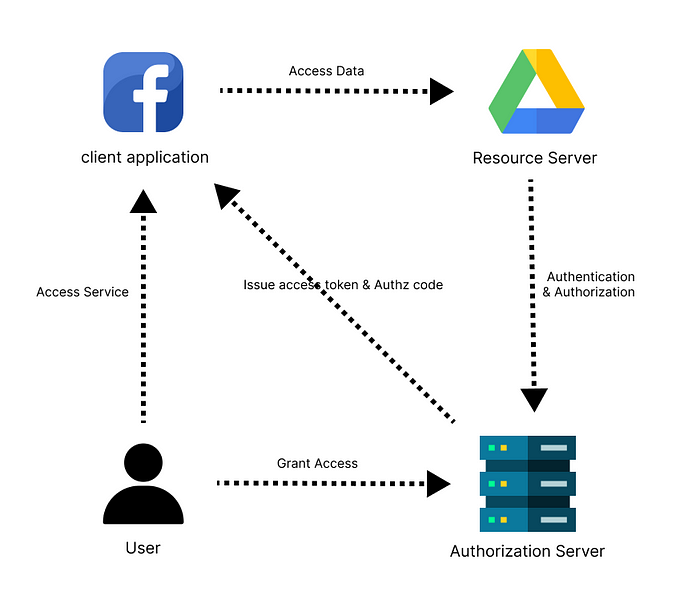
The main objective of using OAuth is to allow client apps to access server resources on behalf of the specific Resource Owner. OAuth additionally enables Resource Owners (Users) to grant limited third-party access to some resource servers without disclosing their credentials. For example, people who log in to LinkedIn with their Gmail account can access their contact list friends who use LinkedIn.
Resource Owner (User):
A component or person that has access to grant access to a protected resource is known as the resource owner. When the resource owner is a person, it is also known as the “end user”.
Resource Server:
Server that has protected resources and is capable of granting resource requests that come in tokens.
Client Application:
An application that acts as a representative of the resource owner, making secure requests while being granted authorization by the resource owner.
Authorization Server:
The server is issuing access tokens and authorization codes to users who have successfully authenticated with the resource server and obtained the authorization.
Responsibilities of authorization server
- Authenticating the users This can be done using different methods, such as username and password, social login, and SAML.
- Obtaining the user’s permission to grant access to the resource server that needed resources.
- Issuing the access token to the client, and that access token is cryptographically signed for that user to access the protected resources.
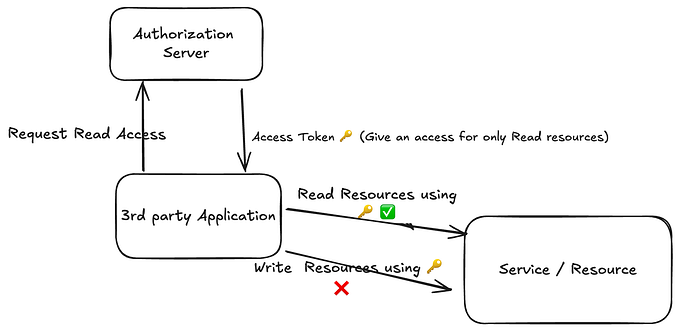
Steps for most common authorization code flow that supports OAuth 2.0
- The user is redirected to the authorization server by the client.
- The authorization server verifies the user’s identity and obtains permission to give access to the secured resources.
- With an authorization code, the authorization server redirects user back to the client.
- The client exchanges the authorization code for an access token from the authorization server.
- The client uses the access token to access the protected resources on behalf of the user.
You must also register your authorization server with the resource servers you intend to support. After you’ve configured your authorization server, you can begin issuing access tokens to clients. Clients can then utilize these access tokens on behalf of their users to access the protected resources.
Benefits of using an OAuth 2.0 authorization server
- Improve the security by avoiding clients having stored users’ credentials
- OAuth 2.0 reduces the risk of theft of information through restricting clients’ access to users’ resources.
- Allows users to log in to applications without having to enter their credentials several times, resulting in a more smooth user experience.
- OAuth 2.0 is a flexible protocol that can be used to support a wide variety of applications and use cases.
Some popular OAuth 2.0 authorization servers
- Auth0
- Okta
- Google Auth
- Microsoft Azure AD
- Amazon Cognito




![Building Microservices [PART-3]: Role-Based Authentication & Authorization — Passing Logged-In…](https://miro.medium.com/v2/resize:fit:679/1*ADql83yQSZ0EDlIx38rfVQ.png)

